Meeting, and exceeding, industry standards for security.


The purpose of an ISO 27001 certification is to provide the establishment, implementation, maintenance and continual improvement of our information security management system – from our people to our processes to our systems – and verified by a third-party independent auditor.

Our information security practices, policies, operations, and procedures meet the Service Organization Control Type 2 requirements for security and privacy. This delivers peace of mind for to spaces and operators that we serve as an enterprise-ready network management platform.

As the world’s most robust privacy and security law, the General Data Protection Regulation, enacted by the European Union, governs how we process and store user personal information. This compliance confirms we meet the highest level of user data security to our customers in Europe and beyond.

Authenticated devices are linked to a user, making it easy to control both user- and device-level access on the network.
All data passing through the isofy software is encrypted via SSH and TLS connections using AES-256 encryption.


isofy maintains a properly configured and up-to-date firewall on all isofy networks.
Unauthenticated devices are segmented into a guest VLAN that is completely isolated, with no local network access or internet access.

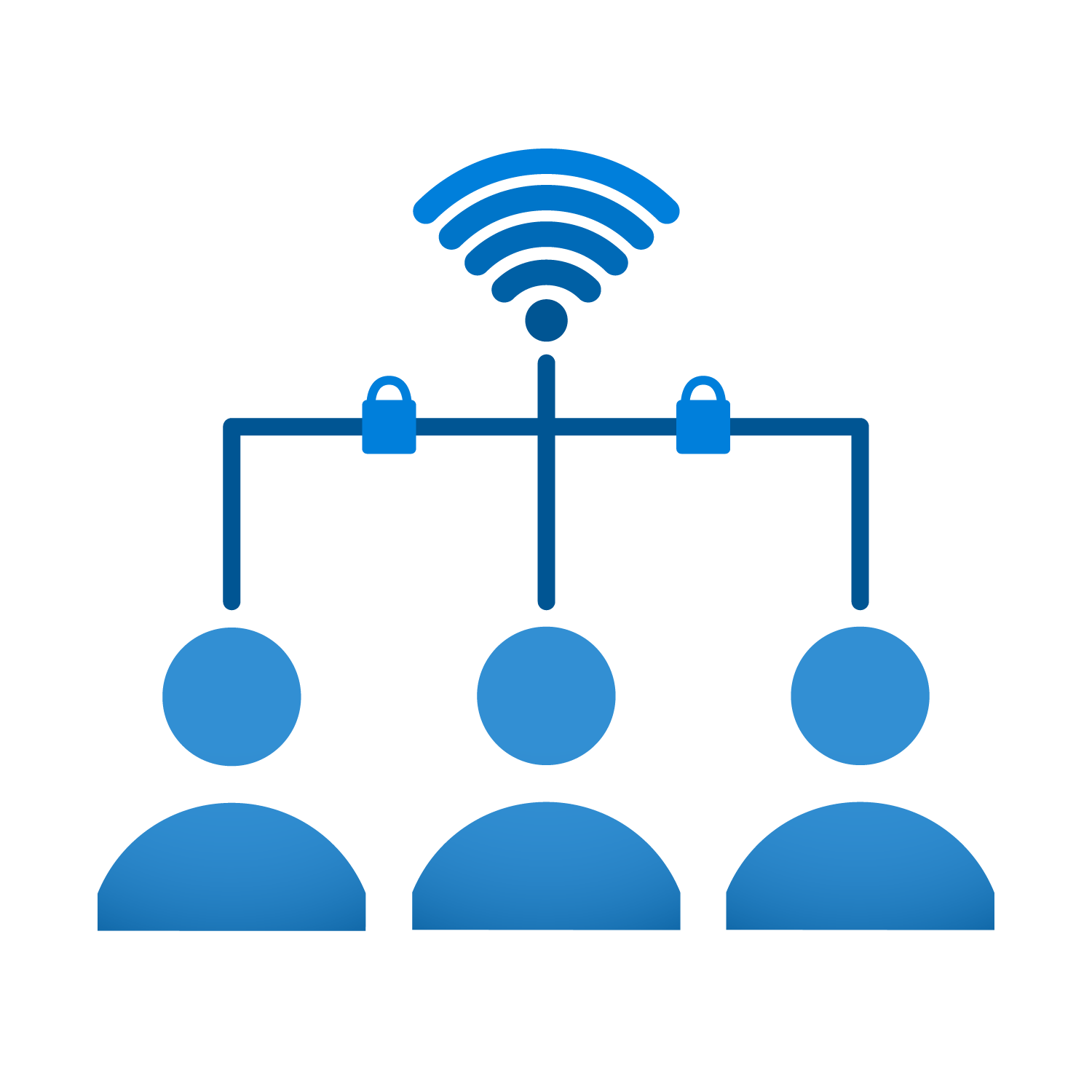
isofy excels at role-based permissions by not only configuring users’ access but also completely and automatically isolating them from each other using VLANs. With isofy, role-based permissions are automatically supplemented by role-based network segmentation.
Each piece of network equipment is individually added to the platform. The network access controller will not allow authentication requests from network equipment that has not been added to the platform.


All actions on the network are automatically logged, and logs are retained for a length of 6 years.